How an Office 365 Email Hack could have cost $Millions and what you should put in place to avoid this happening to you!!
Imagine you’ve just made a multi-million-dollar investment in your business, you completed your research and you are all set to make the $transfer. You press the go button, yet something is bothering you about the last few emails. Why did the investment company change the banking details at the last minute? And why have some of the key people in the deal not weighed in on those changes? It’s a lot of money, and you lose sleep over this.
The next day you review your emails with the investment company and discover everything looks fine except for an old signature being used which catches your eye, a near-undetectable difference. Have you been hacked? Why did this happen?

The fact is you were hacked and you were actually being watched for a long time,
How did they insert themselves into an email chain without being noticed?
How did they know all the relevant names, places, and details going months back?
They knew it all, and now you’ve wired a large sum of money to a stranger.
Could your business survive?
This exact scenario just happened to a client of ours. Here’s the story of how it happened, how CROFTi helped the client deal with the event, and how you can put the proper security procedures in place to prevent this happening and of course your business from being affected.
HOW THE HACK HAPPENED
CROFTi has been brought into this story with a few clients when they asked for our assistance in tracking down suspicious wire transfers. They had nearly been the victim of a million-dollar wire transfer fraud scheme, and they only caught it at the last minute. Thankfully, they were able to contact their bank, report the fraud, and have the transfer cancelled. It took more than 48 agonizing hours for the bank to confirm the cancellation and save their business from losing millions of dollars. It could have gone totally wrong!
They wanted to know how it happened, so our investigation set about uncovering the truth. At some point in the recent past, staff in the organisation had there Office365 accounts compromised. The hackers were able to successfully log onto the client’s Office365 account and set up forwarding rules that sent all received emails to Gmail accounts owned by the hackers. Then, the forwarded messages on the staff office 365 accounts were then deleted to hide the trail that this had even happened in the first place. So sneaky!
All the hackers had to do was watch the Gmail account for discussions of contract negotiations and when a fund transfer was going to take. In this case, it just so happened the hacker had hit the mother load with a million-dollar investment in the works. They created a new rule forwarding any emails about the wire transfer, applied this to multiple email accounts within the organisation, deleted evidence of the forward, and used previous email chains to fake a response.
To the client, aside from the slight change in email signature, the forgery appeared like an actual reply to an ongoing email conversation they were expecting, and the hacker was able to craft a convincing reply about a last-minute change in banking details. The clients thought it was odd but proceeded with the wire transfer. When we say last minute, we mean it. All this happened in a 15 minute window within an email conversation.
Shortly after, they realized something was wrong and got us involved to help them out. The first thing we did was investigate the situation, ran tracers throughout Office 365 to confirm such event had happened and once confirmed proceeded to reset all users Office 365 passwords and remove all rules found within multiple user account inboxes.
We also ran a search through the DarkWeb and found 15 accounts that had been comprised over the year. We then used PowerShell to investigate the Office 365 tenants and found multiple accounts had been hacked, watched and multiple inbox forwards setup.
Next we ran a message trace to all emails sent to the offending Gmail account and we hit reporting limitations for Office 365. The offending Gmail account was reported to Google, Australia Government – Office of Australian Information Commissioner for the Notifiable Data Breaches scheme and the client had to send out a notice to their entire customer database notifying them of the compromised mailbox and potential leaked information.
The cost of a hack like this can cost companies millions, as its not just the hack and the fraud we are talking about, we also need to consider the down time caused throughout the organisation from internal staff members helping with the investigation to the external resources required on the ground throughout the entire process. Not forgetting the amount of stress it puts everyone under.
Moral of the story....aim to protect yourself in the first case. Don’t let this happen to you

How to Protect Your Business against Hackers
There were a number of mitigating security policies clients could have implemented that would have prevented or limited damage from this type of compromise. We’ve outlined some of those strategies below and are recommending all our Office 365 clients to use the recommendations moving forward.
Additionally, we recommend you talk with CROFTi about which strategies at different price points might be most advantageous for your business to implement:

Zero cost mitigation strategies
- Enable two-factor authentication – By creating two-factor authentication, you strengthen your security so only the owner of the token and password can log into Office 365. This does require periodic re-authentication so the token and token authentication on every web login remain secure.
- Disable forwarding rules companywide – This strategy prevents compromised accounts from forwarding emails on autopilot outside the organization.
- Implement complex and rotating passwords – Static passwords are easier to crack. Threats to email accounts are lessened if passwords go through more frequent rotations.
- Urge employees to conduct periodic reviews of mail rules and forwards –This empowers employees to be aware of their own settings and improves their ability to recognize if their account has been compromised.
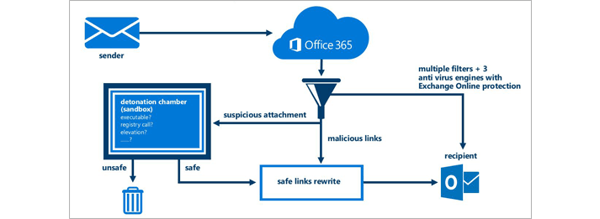
Low cost mitigation strategies
- Use Advanced Threat Protection for Office365 – This solution provides a layer of security from email spoofing and email phishing scams and discourages virus attacks resulting from email and wire transfer/social engineering fraud.
- Train employees on cybersecurity strategies – Employee awareness of email, web, and computer security improves their ability to recognize when anything is amiss and reduce one of the most common cyber threats: employee-caused data breaches.
- DarkWeb Monitoring – this solution allows for your email domain to be monitored on an ongoing basis to ensure your accounts and passwords haven’t been leaked into the darkweb.
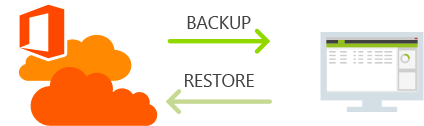
Higher cost mitigation strategies
- Upgrade to E5 Licensing – This Office365 feature provides behaviour analysis alerting and automatic actions. Those range from automatic account lockouts and forced re-authentication to email and geo-location login alerts. E5 licensing is recommended for high risk employees such as executive team members, those involved in finance, executive assistants or influencers in financial transactions.
- Office 365 and SharePoint Backup – this is not a prevention but more a solution to keeping your company running if in the event you are hacked. Ensuring your office 365 and SharePoint data is being backed up at all times allows you to quickly restore if required, minimal downtime for your business.

Reduce Your Risk from Cyber Threats
The threat to your business from data breaches is not going away. Whether through your email or a weak point in your network, hackers will find any vulnerability and try to exploit it. The good news is that CROFTi’s team of trained professionals can help you prepare for threats and put the proper tools and practices in place to prevent and limit damage.
GET PROFESSIONAL IT HELP. Talk to us. We have an excellent team of professional IT Staff ready to educate you and prevent these cyber attacks from happening to you and your company. Visit us at www.crofti.com.au, send us an email at support@crofti.com.au or give us a call at 07 3067 0001.
Don’t wait for this to happen to you or anyone you know. Like and Share this article now.



